How would you explain the internet to a child
Internet - Kids | Britannica Kids
Introduction
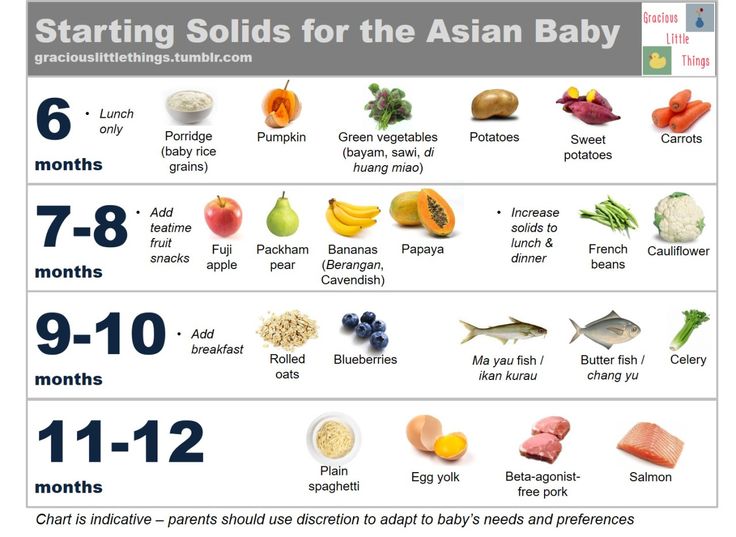
The Internet is a network, or system, that connects millions of computers worldwide. It was one of the greatest inventions of the 1900s.
Since its beginning, the Internet has changed a great deal. Advances in technology have made using the Internet quicker and easier. No longer limited to personal computers, the Internet can be accessed via tablet computers and most cell phones and televisions. As more and more people use the Internet, the quantity of information continues to grow.
History of the Internet
In the 1960s the U.S. government, businesses, and colleges worked together to make a system that would let computers across the United States share information. They created an early form of the Internet called ARPANET in 1969. In 1971 electronic mail, or e-mail, was invented as a way to send a message from one computer to another.
By the mid-1970s many groups of computers were connected in networks. Machines called routers were invented to connect the networks. This is how the original ARPANET eventually grew into the Internet.
In 1989 hypertext was invented. Hypertext is a link between different parts of an electronic document or between different documents. Hypertext became the basis of the World Wide Web, or “the Web,” which was created in the early 1990s.
The World Wide Web
Information on the Web is arranged in sites or pages. People view Web sites using computer programs called Internet browsers. People create Web sites using a code called hypertext markup language, or HTML. Browsers read HTML and allow people to view Web sites on the computer. Each Web site has its own Internet address, called a uniform resource locator, or URL. Many URLs begin with “www,” which stands for “World Wide Web.”
People often use the Web as a part of their schoolwork or job. They use search engines—such as Google, Yahoo!, and Bing—to look for information on the Web. People also use the Web for entertainment. In the early 2000s some of the most popular Web sites were social networking and shopping sites. Facebook, Twitter, Instagram, and Snapchat are social networking sites. They help people communicate with friends. Amazon and eBay are sites for shopping.
In the early 2000s some of the most popular Web sites were social networking and shopping sites. Facebook, Twitter, Instagram, and Snapchat are social networking sites. They help people communicate with friends. Amazon and eBay are sites for shopping.
Internet Safety
There are many ways for people to save documents, e-mail messages, photographs, and videos on the Internet. When people do that they have the option to share what they save with only certain people or to post information so that it is public. Information that a person makes public on the Internet becomes what is known as that person’s digital footprint. It is important for people to think very carefully about what they put online. They should control the information they save online and what is shared with the public.
Many Web sites allow visitors to write messages on a message board or to chat with others that visit the site. These chats can often be read by anyone. It is not easy to know if someone is telling the truth in a chat room. People should never make plans to meet anyone whom they have met and chatted with on the Internet.
People should never make plans to meet anyone whom they have met and chatted with on the Internet.
A person’s real name, e-mail address, telephone number, home address, and school should be kept private. Just as people should never share personal information with strangers, they should never post personal information about themselves for anyone to find. Always get permission from a teacher, parent, or guardian before registering or logging in to a Web site.
Cyberbullying is another way a person may not feel safe on the Internet. A cyberbully puts words, photos, or videos on the Internet to embarrass or threaten another person.
Cybersecurity
Every computer connected to the Internet needs to be protected from cybercrime. Cybercrime is when someone uses a computer to do something illegal. Cybercrimes include hacking, phishing, and the use of malware.
Hackers are users who break into computer systems. Once they gain access to a system, they may steal sensitive information, such as credit card numbers or personal information. Hackers may also expose company or government information that is meant to be kept secret.
Hackers may also expose company or government information that is meant to be kept secret.
Phishing is an e-mail that looks like it comes from a trustworthy source. The e-mail takes the user to a Web site that asks for personal or financial information. This information can then be used by cybercriminals to commit fraud, such as identity theft (using a person’s private information without permission, usually for financial gain).
Like phishing, malware can be sent through e-mail. It can also invade computers through Web sites, software, or hardware. Malware takes over computers. It slows them down and damages data.
Computers can be protected from cybercrime by using cybersecurity such as anti-virus programs and firewalls. Firewalls filter data that travels to computers, phones, or tablets from the Internet to make sure it is safe.
The internet explained for 4 year old kids
Yesterday, after receiving the question that every parent is afraid of, I spent 40 minutes explaining the answer to my 4 year old daughter Nathalie, the answer to the fateful question: Hey Dad, what’s the internet?.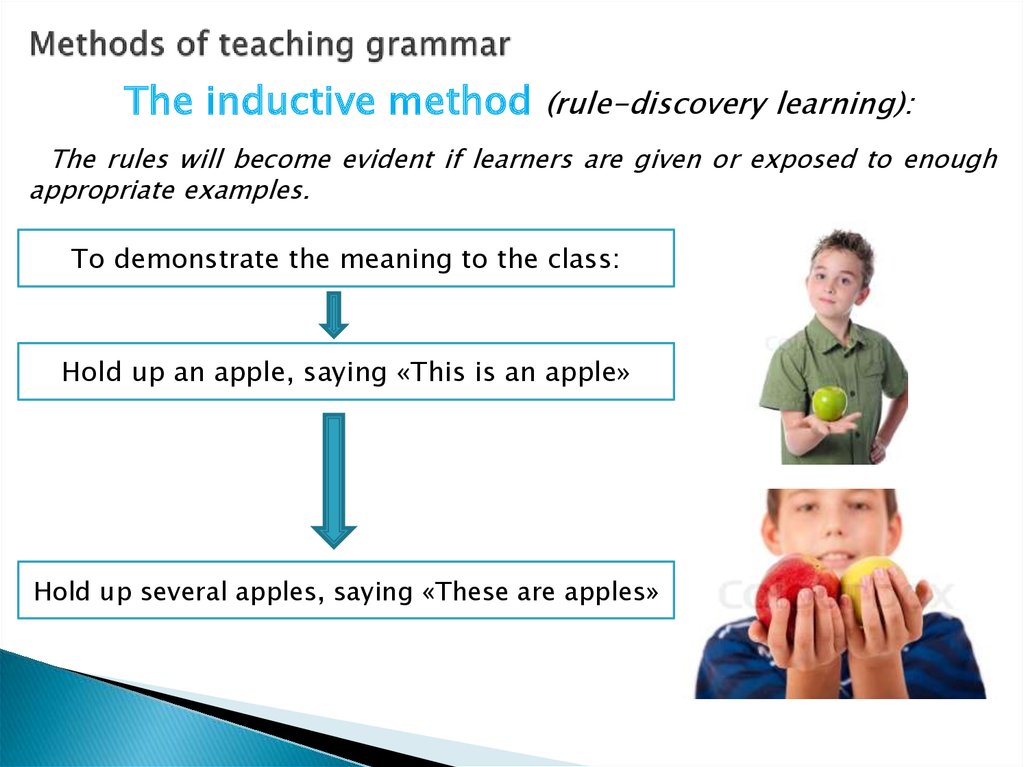
Through many drawings and simple explanations, I was able to make her understand (and I asked her several questions to double check it), once I told about my success on Google Plus, many people asked me to share both the explanation and the drawings and so, here they are.
Before I started discussing computers, digital content and data transfer, I began with a simple example.
Imagine that Nathalie wants to play with the wooden horse of her friend Malu, who lives at 45 minutes of our house, and that there is a underground tunnel that allow us to reach far places rapidly. She will only have to enter the tunnel and she will almost instantly in Malu’s house to play with the horse, then she will be able to come back at any moment.
Now let’s imagine the houses of all the children around the world connected through this tunnel, allowing us to enjoy the toys of every kid at any time, as long as the kid allows it, of course.
Each kid will be able to decide whether he wants to share or not his toys at the tunnel’s entrance, or indicate which ones he wants to share and which ones not.
The example ended here, though I’d probably be able to extend a little bit by telling here that not every house has a tunnel and that is possible that many kids want to play with the same toy at the same time and that it’s not possible to break other kids’ toys (well in fact you can, but that will only make things complicated)
Once she understood the metaphor and I asked all the necessary questions to make sure she have understood all the advantages of having a tunnel like that, we began with the Internet, but not before I show you the drawing I conceived as I was explaining the topic.
Computers, telephones and TV in the magic tube
To explain the internet, I used the world of film-making process as an example. She is acquainted to see online movies as well as on TV. Sometimes we watch cartoons together on YouTube, therefore the word Internet showed up with a certain frequency day after day.
Imagine that we’re watching cartoons on the computer and we want that our friend Malu can watch them as well. One way will be lending her the DVD and wait to have it back the next day, but what if there is a very long tube that can carry the image and sound to Malu’s PC?, that would be much better.
One way will be lending her the DVD and wait to have it back the next day, but what if there is a very long tube that can carry the image and sound to Malu’s PC?, that would be much better.
We build the magic tube and then we ask Malu to hook it to her PC (or her TV, which can also be done). Once the tube is fully operating, we can see the movie with Malu at the same time.
Now connect more computers to the tube and let’s take a glance at what we can observe in them. We see that a child in China has put a new cartoon on the tube, while another kid in Argentina has put some pictures of his latest trip and another boy in France has put his coloring book.
If all the computers were connected between each other, we would be able to see what others see, play the things they play and even talk through the tube so others can listen to us … that’s how she talks with her grandparents, through the magic tube that in this case connects our computer with theirs.
On the same way that the tunnel connects houses, every kid in the world can decide which movies he wants to share, which pictures he want us to see, what games is he going to leave on the tube, etc.
If one day the tube is not functioning, then you will only be able to see what’s inside your computer, therefore you won’t be able to look for videos in other kids’ computers, you will not be able to talk with your grandparents and you will be also unable to find new video games … which is exactly what happens when Daddy says that the internet is down.
You can find many things in those cables, jungle books, underwater photos … anything that other people have created and then put on the tube to share with the rest of the world.
At this point, Nathalie asked me if it was possible to put on the tube the drawing she made yesterday so other kids can see it. I answered yes and that she could even receive opinions and comments about the color she chose for the sky or the style she gave to the flowers.
Just like before, I skipped the fact that the Internet is not only a P2P network, that there are servers and access filters, though once the idea of interconnected computers around the world matures, it will be easy, within a few months, to explain the concept of servers (at the end it’s just adding the concept of big computers with lots of tubes connected to them and a gatekeeper watching over the tubes.
The second drawing is similar to the first one:
Problems found:
- Now she want us to buy a TV with internet connection, just like Malu’s, that way she will be able to see the Argentinian kid photos on a big screen while sitting on the couch.
- When I drew grandpa’s telephone, I made a drawing similar to the ones we make during our childhood, with the earpiece and the little numbers’ wheel … I had to erase it when she told me that she had no clue about what that drawing meant.
- I had to explain her why she cannot put the Snow White DVD on the magic tube, though that explanation was worse than the previous one.
Wwwhat’s New
Founded by Juan Diego Polo, this site discusses all the new web applications, free services, task management, social networking, finding restaurants and many more things that can help you leverage your free time, you can follow all the site’s updates in http://twitter.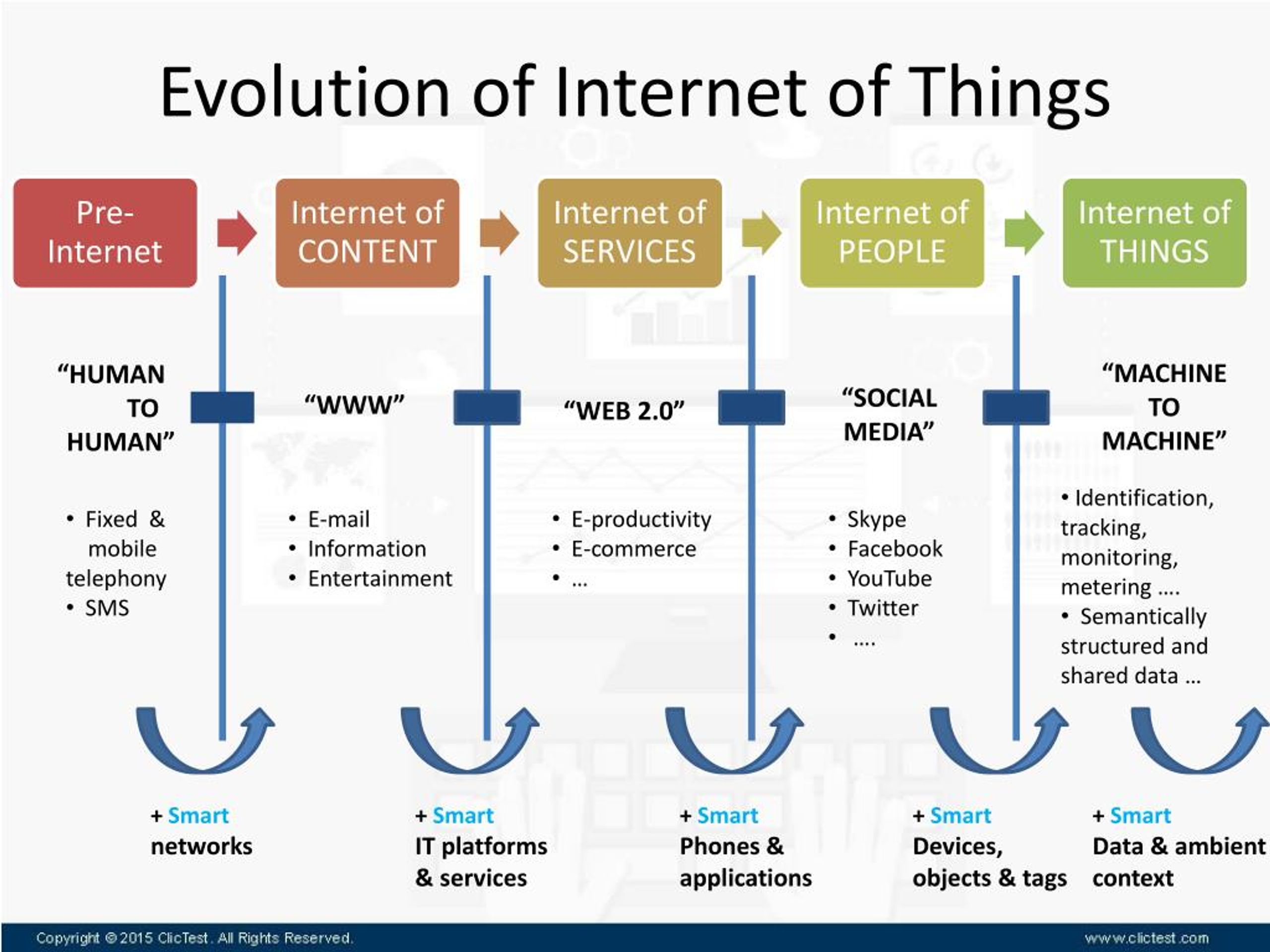 com/wwwhatsnew
com/wwwhatsnew
With the help of parental control and family rules: how to restrict access to the Internet for a child
How to restrict access to the Internet to a child without technical means
According to Yulia Tokarchuk, a researcher at the Center for Interdisciplinary Research of Modern Childhood, MSUPE, the question “How to restrict access to the Internet to a child? » Today, most parents are concerned:
“According to statistics, in Russia, 53% of children spend from one to four hours a day with digital devices, more than a quarter (26%) spend all their free time on them. At the same time, children of primary school age most often use gadgets for playing games and watching cartoons, while teenagers more often use the Internet for communication and entertainment. And if at primary school age parents can technically restrict access to the Internet - with the help of parental control, then in adolescence, the policy of establishing rules for using the Internet will more likely work.
From incorrectly chosen glasses to a tumor: why a child has a headache
About why children have a headache, what medications are allowed to be used...
03 September 09:29
The psychologist explained that it is important to maintain a trusting relationship with the child so that in the event of a potentially dangerous situation, he can turn to you for help. According to the researcher, the introduction of family rules will help to limit access to the Internet for a child: “They can relate to space or time free from digital devices. For example, using gadgets in the kitchen during breakfast, lunch or dinner is not allowed. Or after 20:00, digital devices must be put on charge and access to them is limited.”
Yulia Tokarczuk stressed that such rules will work more effectively if all family members adhere to them:
“The best example in terms of the amount of time spent on the Internet is, of course, you. If an adult himself actively and constantly uses the Internet to the detriment of personal family communication, you should not expect a different behavior from a child.
How to protect a child from adult content on the Internet
Zhanna Meksheneva, Director of the Department of Mathematics of the Faculty of Information Technologies of Synergy University, believes that before restricting access to the Internet, a number of mandatory rules should be identified.
1. It is necessary to clearly regulate which devices a child has access to and which not. So, for example, it is completely unacceptable for him to take his parent's phone without asking and install gaming applications on his own or watch YouTube, which has no age restrictions.
2. Discuss with the child in advance the time of using the gadget. Set a timer with a clock. The child must understand that "work is time, fun is an hour."
3 "Junk" and adult content can enter the gadget under the guise of advertisements or banners. Therefore, it is worth explaining to the child that with the help of parental control you protect him from inappropriate content.
To answer the parent's question, "How can I protect my child from adult content on the Internet?", it's important to understand how parental controls work.
close
100%
How parental control works
Computer science, physics and astronomy teacher Alexander Gromov explained that parental control is a set of algorithms or software that protects a child from malicious, prohibited and unwanted content on the Internet. In addition, with the help of parental control, you can track the movement of the child (sending the geolocation of the device), control his screen time and limit him in online activities (purchases, downloading applications, and so on):
“All this works in conjunction with the parent gadget. The program contains a database of prohibited sites and monitors search engines for the presence of such requests in them, thereby blocking them from a child. Tracks how much time the child spent on his gadget or computer (you can set a limit for a certain time), blocks purchases until one of the parents gives his consent.
How to set a time limit on the Internet
Andrey Sidenko, Head of Children's Online Security at Kaspersky Lab, said that there are technical and non-technical measures of digital care for children that will help control the time they use the Internet:
“Non-technical activities include teaching the basics of online security and time management, as well as building trust between parents and children; technical ones include special settings in applications and services with certain restrictions: for example, some video hosting platforms or game services have special profiles for children, where age-appropriate content is selected. In addition, there are special parental control programs.
In addition, there are special parental control programs.
Parental control apps
You can use the parental control application to make sure that your child is protected from inappropriate content on the Internet:
"A child may have panic attacks and suicidal thoughts": why children should not be beaten
In some families, physical punishment of children is practiced among "education methods". However, many...
September 06 13:22
“The range of applications for parental control is large, so we make the choice based on the principles: understandable, convenient and effective. It is also necessary to take into account the compatibility of the application with Android and iOS, the ability to filter websites, the availability of geolocation services and the prohibition of installing and uninstalling applications. You can spend more than one hour in the application settings, but it's worth it. To block certain online resources, you can use parental control applications such as Safe Browser, LOCKit, Google Family Link, or others,” Meksheneva said.
Computer science teacher Gromov noted that parental control applications are divided into categories according to the operating systems used (for example, parental control on Android), according to the Internet access devices used, and also according to functionality. The expert proposed to consider the last point in more detail.
● So-called "adblockers" that block ads, unauthorized and authorized transitions to third-party sites with content prohibited for children.
● Navigation systems that help parents determine where the child is in real time (assuming that the phone is always with him), they include geolocation on the child's phone and send it to parents.
● Applications that track the screen time of a gadget or computer. They give parents the opportunity to control the child's time spent on the Internet, and they can be used not only for regulation purposes, but also for reward purposes (the child received good grades - increase the time).
● Blockers prohibit transactions and installation of any software on devices, create conditions under which the child will not be able to use finances and third-party applications until the consent of the parent is given.
● Spy monitors all activities of the child in the device, sending a report to the parents.
● Hybrids are programs that combine some or all of the above features.
Parental control through a router
Zhanna Meksheneva explained how to restrict access to the Internet for a child with an advanced level of gadget use:
“Children sometimes start looking for ways to bypass the security account lock, up to and including “resetting” the gadget to factory settings. Therefore, you can consider the second option - to set parental control through the router. Most router manufacturers incorporate tools into their device firmware to block inappropriate content and/or schedule access. Configuration is carried out by MAC address, but there are no universal instructions for configuring models from different manufacturers.
close
100%
How to block the Internet on the phone
An employee of the Faculty of Information Technology noted that in extreme cases you have to block the Internet on the child’s phone:
“This function is deactivated completely or temporarily through the communication provider. It is also possible to block home Wi-Fi. To do this, you need to know the password, but it may not be in public access networks. It is possible to set the minimum amount of traffic for using Wi-Fi for a certain period. The option is available in every modern smartphone through "Settings".
It is also possible to block home Wi-Fi. To do this, you need to know the password, but it may not be in public access networks. It is possible to set the minimum amount of traffic for using Wi-Fi for a certain period. The option is available in every modern smartphone through "Settings".
At the same time, Andrey Sidenko, an expert in children's online security, emphasized that as a child grows up, more and more freedom should be given:
“From the point of view of parental control programs, we recommend leaving only notifications, not blocking. A teenager will still find what he wants, the program in this case will help parents to be aware of his interests.”
How to restrict access to the Internet from the phone
Andrey Sidenko pointed out that before giving a child a smartphone or tablet, you should take care of the settings in advance in order to restrict access to the Internet to a child:
“These can be built-in settings of the phone itself, “children's modes” in popular services, gaming and video platforms, certain parameters in a parental control solution.
Combine settings that allow you to limit the amount of time you use your device with an explanation of why you are doing it: the rules you set in your family should be clear and understandable.
It is better if all family members observe them. For example, if you agreed with your child that you can’t use gadgets during lunch, try to give up this habit yourself. In this case, it will not be perceived as a punishment or a senseless ban.”
close
100%
How to restrict access to applications by time
Alexander Gromov clarified that parental control is by default embedded not only in all operating systems (iOS., Windows, Android), but also in applications in which may potentially contain adult content that is inappropriate for children. User accounts will help take care of protection:
“For this, you can create a separate account (marked “for a child”). All adult content will be blocked on such an account. Antiviruses also have a parental control setting in their functionality.
The advantage of parental control programs is that they do not curtail the main functionality of devices and allow you to build flexible restrictions, Andrey Sidenko noted: “For example, restrict access to Internet resources (both to certain and to entire categories of sites: with obscene language and other categories of resources that are inappropriate by age), control the time of using the device as a whole, restrict access to certain programs, content by age rating, and much more.
How to keep your child safe on the Internet Anita Vayakanti
Internet safety is one of the most exciting topics for parents.
You have probably already seen these social videos in which a young man (in agreement with his parents) creates a fake account and gets to know their children. Correspondence lasts about a week (+/-). After that, the young man, on behalf of the fake account, offers to either meet the child on neutral territory, or come to visit him himself (attention!) when the parents are NOT AT HOME.
And how do you think it all ended? Kids AGREE! They let them into the house / secretly went out to meet with their Internet friend. Of course, their parents and the organizer of this experiment were waiting for them there.
In fact, 10 out of 10 parents said:
- Our (a) definitely will not agree to a meeting. We then explained to him / her that it was not safe. He/she knows everything.
What does this say?
The fact that children do not perceive our moralizing and teachings about the Internet, especially when parents themselves are not advanced users of social networks, that is, they do not have any authoritative opinion in this area.
Moreover, we adults often condemn children's Internet hobbies, all these applications like Like , TIk Tok , etc.
Therefore, I want to offer you a slightly different approach to protecting children on the Internet.
1. YOU NEED TO FIND OUT FOR YOURSELF WHAT IS POPULAR NOW
Do not be a dinosaur for your children who has just crawled out of his cave and knows what Odnoklassniki is.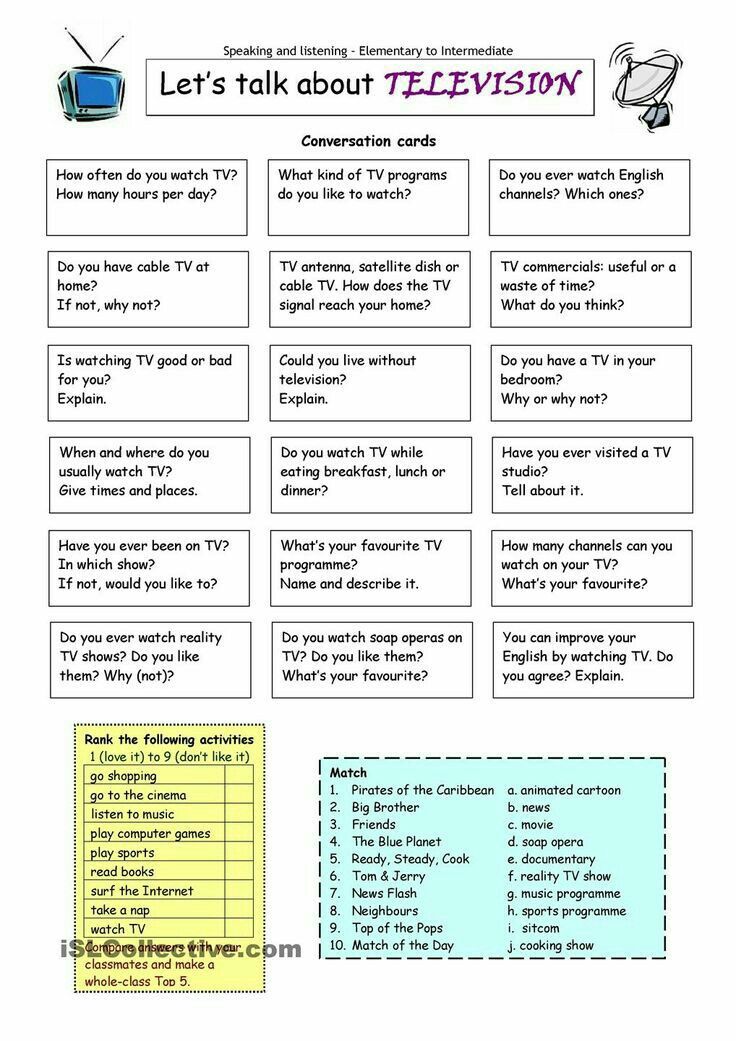 Learn what your child likes, why, and how he finds himself in it. After all, even in the same “Like”, a child learns to edit videos, apply music and some kind of filters and, most importantly, is NOT shy and shows himself and his creativity.
Learn what your child likes, why, and how he finds himself in it. After all, even in the same “Like”, a child learns to edit videos, apply music and some kind of filters and, most importantly, is NOT shy and shows himself and his creativity.
Look at the child's account. Maybe there is something cool there, or maybe something unacceptable (I will tell you about this below. And yes, a child under 14 can and should consult with their parents about the content that they post). In general, get involved in the Internet world of modern children.
2. YOU NEED TO BUILD TRUST WITH YOUR CHILD
Trust is a guarantee that parents know what is going on in the life and in the soul of the child.
Remember that trust means communication, acceptance and non-judgment. I wrote a lot about how to build relationships with children so that they are trusting.
And yet, do not forget that relationships are work, and it is better to start working from childhood.
It is very difficult to establish contact with a child already in adolescence, if before that there were many omissions and mistakes
Just to make sure that your child as a teenager is not so "biting", my colleague and I are preparing an online program "What a teenager is silent about." Who cares - write.
3. TELL YOUR CHILD (starting from 6-8 years old) ABOUT THE RULES OF CONDUCT ON THE INTERNET
It is interesting to tell stories with personal examples.
Let me share with you how I do it in group/private lessons.
First we start a conversation with the children/child. About anything. About hobbies, fashion, modern music, cartoons, etc. All this smoothly flows into the Internet, social networks, applications.
And I ask:
- Do you think the Internet is safe or there might be something dangerous there?
(most often children assume that there is some kind of danger there)
- Do children, and adults too, need to follow the rules of behavior on the Internet?
(most often I hear a positive answer to this question)
- Why do you think so? After all, no one can touch you there. There are no roads on which cars can pass at great speed. Why are there rules in the Internet space?
There are no roads on which cars can pass at great speed. Why are there rules in the Internet space?
child/children offers its options.
After that, I agree with what was said, maybe I supplement somewhere and say the following:
- Yes, everything you said is right. There are two dangers on the Internet:
1. One that can hurt you, your personality, your feelings, etc. (these are scammers, haters, adults who can impersonate others to meet a child, angry and scary sites).
2. The second one, which can harm your equipment and personal data (these are viruses, hackers, etc.).
Then I MUST convey to the child that I believe that he already knows all these rules and adheres to them:
- Well, I definitely don’t worry about you, you know how to behave on the Internet, but let's go let's talk about it together again, in case I'm missing something.
- Let's first discuss how you can secure your equipment and personal data?
And together with the child we pronounce or fix (in a notebook, on the board) in the form of a table (I really love tables :)) what can and cannot be done.
For example:
DO NOT:
1. Set easy and identical passwords in social networks.
2. Share your passwords with friends.
3. Follow links that strangers and even friends send without warning (here I tell a personal example).
4. Register in unofficial applications and leave a password for your social networks there.
5. Send money, etc.
POSSIBLE:
1. Set complex passwords (example).
2. Share these passwords with your parents.
3. When creating an account in social networks, specify the parent e-mail as a backup.
4. Install an antivirus on the computer.
5. Download ONLY licensed applications (fortunately now only such in the app store and google pay), etc.
We made a beautiful sign. Discussed and, as a result, remembered. Next, we move on to the most, in my opinion, important thing - directly the safety of the child.
4. YOU NEED TO TELL YOUR CHILD ABOUT MARKER WORDS
After all, children, unlike adults, can not so clearly filter both accounts (fake not fake) and people's intentions. Therefore, it is very important to talk about marker words, which, let's say, may indicate that a bad person is sitting on the other side of the screen.
Therefore, it is very important to talk about marker words, which, let's say, may indicate that a bad person is sitting on the other side of the screen.
WHAT CAN THE WORDS MARKERS BE?
- Hello! You are so beautiful, post a photo!
- Where exactly do you live? What is the house number?
- Are you an adult already? Do you often stay at home alone?
- And what do your parents do? Do they go to work every day?
- Drop your geolocation!
- How old are you? Are you already dating boys/girls? etc.
It is important to explain to the child that these marker words can be written a little differently, the main thing is that the meaning remains the same.
Next, we tell the child that when he sees this kind of message, it is important for him to TELL MOM/DAD ABOUT THIS. This is where the trusting communication that I mentioned above comes in handy.
It is important for a child to show the profile of this person so that mom or dad can help to figure out if this is a real boy / girl or an intruder.
If the profile is suspicious, then inform the child that this user needs to be blocked, as this is a bad person. And of course, THANK the child for telling us about it.
Diagram clear? Let's repeat.
Marker words -> saw -> told mom -> analyzed the account together -> (if something is suspicious - block) -> thank the child both for showing and for tracking.
JUNIOR SCHOOLCHILDREN (up to 10 years old) CAN READ an interesting FAIRY TALE "ABOUT SECURITY ON THE INTERNET" - write in the comments if you are interested in a fairy tale, and I will send it to you.
5. YOU SHOULD CHECK THE ACCOUNT (and content) OF THE CHILD
Trust, trust. And it's worth monitoring the child's social networks.
Discuss with your child in advance which photos/videos are acceptable to share and which are not, and WHY. It is important to argue this and not be a hypocrite.
And let's be honest, 90% of parents read their children's correspondence. BUT! It is important not to say to your children:
BUT! It is important not to say to your children:
Why do you use these words? Did you skip school? What are these ideas, etc.
If you read correspondence and comments of a child, monitor his friends, then remember that you are not doing this in order to reprimand the child for swearing, cigarettes or absenteeism, but in order to SAFE him from ill-wishers. This thought should be motivation, not total control.
If we see some suspicious activity on the page of a child, a strange user and correspondence, then we gently help the child come to the conclusion that this may not be the person he claims to be.
We ask questions. We remind you of marker words. We tell (invent) cases from life and DO NOT condemn (the child) for this communication.
In general, I would recommend that classes on “SAFE INTERNET” be made compulsory in schools and held once a month or once every two months. Repetition, as they say, is the mother of learning.