How to acess child porn
Finding child porn and Daily Show clips… without hashes or keywords
Biz & IT —
Nate Anderson -
LTU Technologies has made its name with image search tools. That might not sound interesting until you think of all the different ways that such tools can be used: identifying child pornography, stopping copyright violations, checking that stock photos only end up in proper locations. As LTU launches an update to its flagship Image-Seeker software, I spoke with company vice president Kevin Smith about how LTU's "image DNA" can provide better image identification than hash-based technologies and how it's already doing so for cops and companies around the world.
Finding child porn can be tough business, even when you have a suspect's computer in hand. The images you're looking for could be called anything and located anywhere; file extensions might have been altered. The computer could contain tens of thousands of pictures. Some might be hidden.
So to do the job, the entire contents of a suspect's hard drive are dumped into a massive log file in the widely-used forensic examination tool EnCase. LTU's Image-Seeker can function as a plug-in for EnCase, and it scans the log file for images. Once these are identified, the software generates "image DNA" for each picture. The DNA is a unique identifier that is based on a pixel-level examination of color, shapes, textures, object arrangement, and other elements. The result is a unique identifier that is far more robust than a simple file hash (which can be fooled by making just tiny tweaks to an image).
In the LTU system, images can never be identified in a vacuum; context is everything. Before the system can even function, it needs to be trained using databases of images. LTU has created several of its own, including a 50,000-image database of pornography. Coupled with this database, the software is generally able to handle pictures that have been resized, cropped, inverted, and had faces blacked out, all of which would be more difficult with hashes.
LTU has created several of its own, including a 50,000-image database of pornography. Coupled with this database, the software is generally able to handle pictures that have been resized, cropped, inverted, and had faces blacked out, all of which would be more difficult with hashes.
Smith notes that in order to properly classify newly discovered images as pornographic, the database must constantly be updated to stay on top of the latest porn trends. Over the course of the last 20 months, this has meant that the database has been jammed with animated porn and low-quality cell phone porn, both of which have exploded in popularity online.
AdvertisementPicture courtesy LTU Technologies
In child porn investigations, this sort of database might be useful for turning up images, but police generally will use a more specific law enforcement database of child porn images to see if something similar turns up on the suspect's computer. They can also seed the database with specific images of a child and then search for matches.
They can also seed the database with specific images of a child and then search for matches.
LTU already counts the French police, the Italian police, the FBI, and the Department of Homeland Security among its worldwide customers.
More than a porn filter
Such tools can also be useful in the enterprise. Last week, LTU launched Image-Seeker 2.0, which features additional tools that make it easy to use the technology to keep an eye on corporate networks. It's not just about technology (though this is a real issue for companies). It's also about violent images, corporate blueprints, and trade secrets; Smith claims that if you can define something visually, Image-Seeker can build a profile to help find it.
Accuracy obviously depends on the type of content, the database used to train the engine, and the kind of search being run. Smith claims 90 percent accuracy out of the box, though this is often tuned for specific deployments. "Customers are understanding that 90 to 95 percent accuracy is generally pretty good," he says. And companies or law-enforcement agencies that want to deploy such technology need to understand that a machine alone will never do all the work. At best, the computer can filter out the extremes, present likely matches, and can then let humans focus on making the necessary decisions.
And companies or law-enforcement agencies that want to deploy such technology need to understand that a machine alone will never do all the work. At best, the computer can filter out the extremes, present likely matches, and can then let humans focus on making the necessary decisions.
Although the technology was developed for still images, it can also be applied to video by processing keyframes. Just as with still images, the database needs to be trained with known material, and it then performs the "image DNA" analysis on every x number of frames. This is then compared to video coming into the system in order to flag content that may be controlled by a content owner.
Such a system has obvious applications for video-sharing sites, including MySpace and YouTube. LTU won't say who it is currently working with, but it already uses its technology in this way. Smith says that the goal, though, is not just to block content but also to divvy up ad revenue and make payments—for instance, when a user uploads a clip containing a 50 Cent track in the background, the music label could get a cut of ad revenue from that video.
LTU is entering a red-hot field by adapting its tech for video-sharing sites. We've already profiled companies like MotionDSP that exist to help web companies solve these thorny content problems, but to date, no one is willing to go on record about what they're up to.
The Dark Web: What You Need to Know
Despite its negative connotations, the Dark Web is nothing to be afraid of. Few know that the Dark Web was actually thought out as a means of preserving privacy and security. However, this also enabled it to become a breeding ground for illegal activity.
There are certainly things to be distrustful of when navigating the Dark Web, and before venturing into it head-first, you should understand certain things about it.
What is the Dark Web?
The first thing you need to know is that there is no actual database for the Dark Web. Instead, there are only what are known as “peer to peer connections”, which means that the data you are accessing is not stored in just one place.![]()
Instead, it is found on thousands of different computers that are part of the network, so that no one can actually identify where the information is coming from. You can upload to the network, but when downloading, there is no telling where you’re getting the data from.
Why do people use the Dark Web?
There are all kinds of uses for the dark web. Some of them are downright nefarious; others, not so much.
- Drug sales
Taking into consideration the anonymous nature of the Dark Web, it was only a matter of time before it came into use to sell illegal drugs. It is the ideal avenue for this kind of transaction, because of the anonymity factor that is inherent to the Dark Web.
- Illegal commerce
To say that you can buy anything on the Dark Web would be an understatement. Anything you can imagine, no matter how gruesome, can be purchased on the Dark Web, from guns to stolen data to organs.
- Child porn
Is it really a surprise that child porn is rampant on the Dark Web? It’s one of the darker aspects of it, but the anonymous nature of it does lend itself to concealing horrible realities like this.
- Communication
For all its negative connotations and activities, the Dark Web can also be a way to foster open communication that can sometimes save lives or make a change. Especially in cases where governments monitor online activity, having a place to speak out freely can be invaluable.
- Reporting
The Dark Web can be used as an excellent source for journalists because sources can remain anonymous. Additionally, no one can track their activity, so it cannot attract consequences from authorities.
How to access
You may be wondering how you can access the Dark Web – after all, you can’t just Google it or access it in a regular browser.
Here are some of the aspects you need to keep in mind about accessibility, including the browser you need to use, the URLs, personal credentials you may need, and even acceptable currency, should you decide to make a purchase.
- TOR browser
The most common way to access the Dark Web is via The Onion Router (TOR), the browser used by most people for this purpose. This ensures that your identity will remain concealed, as will your activity, because it encrypts everything.
You can obtain the TOR browser by downloading it from the official website. It’s as easy as installing it and running it like any normal program. And if you were worried about the legality of it – have no fear.
Both accessing the Dark Web and downloading the means to do so are entirely legal. While this can enable some pretty dark human behavior, it can also give us very necessary freedom to do positive things, as you will see. Not everyone uses it for nefarious purposes.
- Exact URLs
Something that makes it difficult to navigate the Dark Web is the fact that the pages are not indexed by browsers. That means that anything you may be looking for will require an exact URL. That does limit the amount of people who can access the Dark Web, as well as the scope of the pages one can gain access to.
That does limit the amount of people who can access the Dark Web, as well as the scope of the pages one can gain access to.
Unless you know exactly where to look, you may not have a lot of luck finding what you want. That can deter you from searching, or on the contrary, it can determine you to go looking for someone who is well versed in illegal activity and who can help you out.
- Criminal activity
It comes as no surprise that the Dark Web is a hotbed of criminal activity. No one is advocating that one pick up criminal undertakings in order to use the Dark Web. But generally speaking, the people who will most likely be looking to access URLs here are people who are engaged in all manner of criminal activity.
- Bitcoin
All transactions on the Dark Web are completed via Bitcoin, as this type of currency cannot be traced. That increases the degree of safety of the transaction, both for buyers and for sellers.
However, that does not mean that these transactions are always safe. There is a high degree of uncertainty that accompanies these transactions, regardless of what you are purchasing.
You might find that the person you are buying from is a scammer who can end up taking your money, but not sending over your product. While identities are protected, transactions are not, so a degree of care is always necessary.
The future of the Dark Web
While authorities are always making efforts to cut down on the number of sites present on the Dark Web, more are always created. In the end, it proves to be a bit of a wasted effort. The more websites get shut down, the more pop up in their place.
Does that mean that the Dark Web will continue in perpetuity? No one can say with any degree of certainty. It is entirely possible that people will seek refuge in the anonymity of the Dark Web as the degree of surveillance grows, or the opposite can happen and we can grow to accept surveillance as a means of ensuring a thin veneer of security.
Conclusion
The Dark Web will always be controversial, but it’s not nearly as scary as it seems. It’s true that it certainly conceals some illegal and immoral behavior, but it can also be used for good. The anonymous and untraceable aspects of it help it remain a somewhat neutral space where one can find the freedom to communicate, investigate, search, trade, make purchases, etc.
Article 301-1 CC. Responsibility for obtaining access to child pornography
If you need the services of a lawyer under Article 301-1 of the Criminal Code of Ukraine, click the selected messenger option or use the phone number listed on the site. Experience in law since 2004.
In order to protect the children of Ukraine from sexual abuse and exploitation and toughen responsibility for committing such illegal acts, in February 2021, the relevant amendments to the Law “On Child Protection” were adopted, which necessitated amendments to the Criminal Code and Code of Criminal Procedure of Ukraine.
In addition to changing existing norms, the Criminal Code was supplemented with new articles that establish liability for:
- harassment of a child for sexual purposes;
- gaining access to child pornography.
It is on obtaining access to child pornography that we will dwell in more detail in this article. First of all, it is worth noting that such a criminal offense (Article 301-1 of the Criminal Code) can be committed exclusively intentionally.
Gaining access is possible in several ways:
- using information and telecommunication systems;
- modern technologies;
- purchase;
- storage;
- import to the territory of Ukraine;
- transport of materials.
The legislator also singles out other ways of committing such a crime:
- acquisition or access to materials containing child pornography for the purpose of sale or distribution;
- manufacture of such products;
- engaging a person under the age of 18 in the creation of child pornography.
Child pornography should be understood as images, videos, etc., which depict persons under the age of majority in the nude, where the genitals or sexual activities are clearly shown - real or staged.
Not only in Ukraine, but also in a number of other countries of the world there is a ban on the distribution of such materials. Violation of this prohibition is subject to criminal liability.
Contents
|
Criminal liability for gaining access to child pornography
As already mentioned, liability for such an act, which is clearly illegal, is established by Article 301-1 of the Criminal Code of Ukraine, which supplemented the Criminal Code in February this year.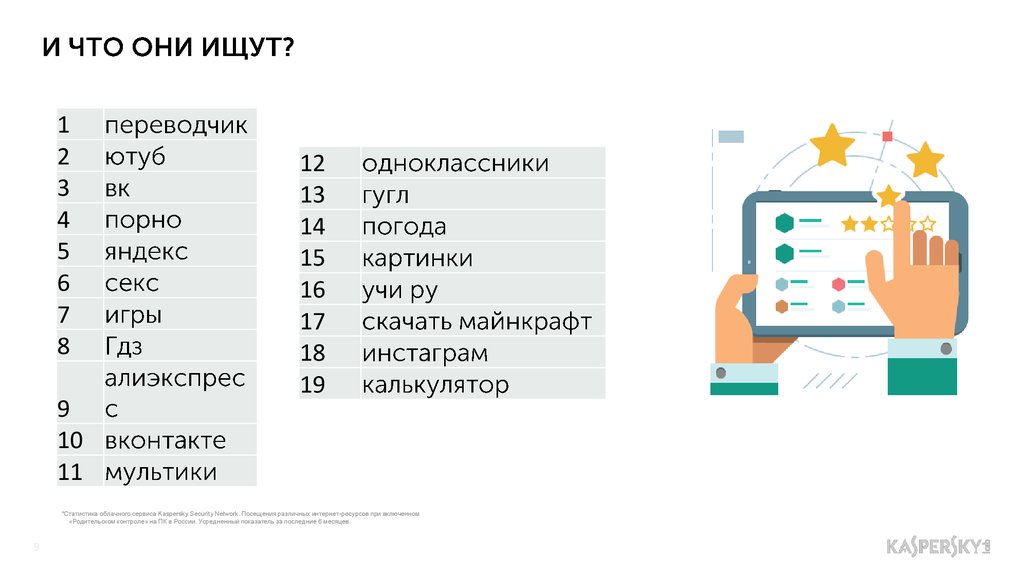
For gaining access to materials containing signs of child pornography without the intent to sell, one of the following penalties may be imposed on the perpetrator:
- arrest for up to six months;
- restriction of freedom up to 5 years;
- imprisonment for a term of two to six years.
An additional penalty of deprivation of a special right may also be applied, the maximum term of which is three years.
If a person has imported child pornography into the territory of Ukraine for the purpose of sale, then he is threatened with:
- imprisonment for a term of 7-10 years;
- deprivation of a special right up to 3 years.
Stricter punishment is provided for the commission of illegal acts aimed at creating child pornography with coercion of minors. In this case, the perpetrator faces up to 12 years in prison, as well as deprivation of a special right.
If there are aggravating factors such as committing a crime in groups, obtaining a large income, or forcing minors to create pornography, the court may impose a sentence of 12 to 15 years in prison.
Minors involved in the creation of pornographic materials are not subject to criminal liability if the above materials were created without the purpose of distribution / sale.
What to do if charged with accessing, acquiring, possessing, importing, transporting, or otherwise moving, making, selling, or distributing child pornography
You have become a suspect in criminal proceedings under Art. 301-1 of the Criminal Code of Ukraine? First of all, conclude an agreement on the provision of legal assistance with a lawyer. It is best not to give any explanations or testimony without the participation of a defender. The defender, after a detailed study of the materials of criminal proceedings, will be able to build a line of conduct and tactics for protecting his client.
If you are detained, relatives, family members, friends can contact a lawyer.
If you doubt the objectivity, competence and legality of the actions of the investigator, use your constitutional right and refuse to testify.
What to do if you are a victim of a crime under art. 301-1 of the Criminal Code of Ukraine
In most cases, such illegal actions not only violate the law, but also bring significant harm to the victims, especially when it comes to young and underage children.
Engaging children in the creation of pornographic materials can cause severe emotional shock, childhood trauma. To prevent this from happening, you need to timely resort to the help of psychologists.
Also, to protect your rights and interests as a victim, you should contact a lawyer. If the victim is a person under the age of 18, his legal representatives — parents, guardians — are entitled to apply to a lawyer.
A criminal lawyer will help protect your rights and recover moral damages caused by a crime.
The fight against child pornography on the Internet: the example of France
The Internet has taken a significant place in the life of a modern person, as it turned out to be an excellent tool for obtaining a variety of information, work and entertainment. However, it can also become a risk zone, especially for the most vulnerable category of the population - children and adolescents.
However, it can also become a risk zone, especially for the most vulnerable category of the population - children and adolescents.
Children and teenagers especially like the opportunity to connect with other people, for example through chats, online games, contests or surveys. However, this poses a threat to their confidentiality and opens up the possibility of falling into the zone of influence of intruders, who are sometimes easy to get the interest and attention of underage Internet users.
Thus, 4 out of 10 children voluntarily or unwittingly encounter offensive content on the Internet, for example, when searching for information, or get virally on certain sites with illegal information. One of the main threats to children in particular is being drawn into pornography. Easy access to the Internet, and more specifically, to the relevant sites, further exacerbates the situation. In addition, anonymity on the Internet contributes to greater trust and propensity for the revelations of users, i. e. those qualities that in real life may not manifest themselves. The perpetrators use this to quickly establish a trusting relationship with children, pressing on the weaknesses of the still fragile consciousness and low sense of self-preservation.
e. those qualities that in real life may not manifest themselves. The perpetrators use this to quickly establish a trusting relationship with children, pressing on the weaknesses of the still fragile consciousness and low sense of self-preservation.
In recent years, a new phenomenon has also emerged regarding the distribution of pornographic materials, including videos and photographs, between teenagers. For example, girls send such materials to their partners, which are then distributed over the Internet, both targeted and to an unlimited circle of people, of course, against the will of the girls themselves. In addition to the moral component, as well as violations of the law, it is worth noting that in the future it is difficult to remove such materials completely from the Internet, and there is a high probability that after some, short or long time, these materials will “emerge” again.
To illustrate the problem, let's look at the situation and specific measures to combat child pornography using the example of France. French law contains rules that minors must be protected from accessing material on the Internet that is "pornographic", "violent", "racist" or otherwise degrading or degrading. Such materials are classified as "harmful" for children and adolescents.
French law contains rules that minors must be protected from accessing material on the Internet that is "pornographic", "violent", "racist" or otherwise degrading or degrading. Such materials are classified as "harmful" for children and adolescents.
These regulations include: French Law No. 98-468 of June 17, 1998 on the prevention and punishment of sexual offenses and the protection of minors, French Law no. No. 2007-297 of March 5, 2007 on the prevention of crime in the media, in which the protection of children occupies a special place.
The fight against child pornography on the Internet has forced the French government to take tough measures to strengthen the protection of minors. At the same time, French legislation, including within the framework of the French Criminal Code (French Criminal Code), provides for sanctions against the transmission of pornographic messages to minors, increasing the responsibility for the direct involvement of a child in such illegal activities, as well as the further distribution of pornographic materials. In addition, punishment is provided for both users and owners of resources for storing such materials. However, in wider resources, with a complex control system, if the owners, for objective reasons, are not able to control all the content of the resource, they may not be held liable.
In addition, punishment is provided for both users and owners of resources for storing such materials. However, in wider resources, with a complex control system, if the owners, for objective reasons, are not able to control all the content of the resource, they may not be held liable.
In France, the law provides for punishment for producers of images of child pornography (art. 227-23 of the French Criminal Code), consumers and persons who have committed a direct crime against a child, as well as persons using telecommunications networks to exploit children in the field of pornography and distribution relevant materials (Art. 227-24 of the French Criminal Code).
In 1990, France ratified the 1989 Convention on the Rights of the Child. In 2003, it also ratified two additional protocols to the Convention: the 2002 Optional Protocols on the sale of children, child prostitution and child pornography and the involvement of children in armed conflict. In 2016, France ratified the third additional protocol to the Convention, namely the 2011 Optional Protocol on a communications procedure.
In general, France is a party to all major international human rights instruments, with the exception of the 1990 International Convention on the Protection of the Rights of All Migrant Workers and Members of Their Families.
In 1990, France ratified International Labor Organization (ILO) Convention No. 138 concerning the Minimum Age for Admission to Employment, 1973, and in 2001, Convention No. 182 concerning the Prohibition and Immediate Action for the Elimination of the Worst Forms of Child Labor, 1999. At 19In 1998, France also ratified the 1993 Convention for the Protection of Children and Cooperation with regard to Foreign Adoption and, in 2002, the Protocol to Prevent, Suppress and Punish Trafficking in Persons, Especially Women and Children, supplementing the 2000 United Nations Convention against Transnational Organized Crime .
As a member of the European Union and the Council of Europe, France has ratified a large number of regional instruments, including the 2007 European Convention on the Exercise of Children's Rights and the 2010 Council of Europe Convention on the Protection of Children against Sexual Exploitation and Sexual Abuse.
In addition, France has implemented the legal framework developed within the European Union (EU), such as European Council Framework Decision 2004/68/JHA of 22 December 2003 on combating the sexual exploitation of children and child pornography, which provides for the punishment of exploitation of children below the age of sexual consent under national law. Although such consent in France occurs at the age of 15, under domestic French law, a child is considered to be a person under the age of 18. Meanwhile, the criminal law provides for sanctions for involving children in pornography, i.e. persons whose age at the time of the commission of the crime against them did not reach 18 years.
Further, the aforementioned Law No. 2007-297 of March 5, 2007 introduced the responsibility of the web host, which is obliged to check the posted materials for violations of children's rights, as well as to involve qualified specialists to carry out preventive measures.
Law No. 2011-267 of March 14, 2011 revised the mechanism provided by the Law on Trust in the Electronic Economy of June 21, 2004, and obligated Internet service providers to block access to sites containing child pornography. At the same time, the police monitor compliance with this mechanism, including by introducing into the so-called. "black list" of Internet sites that continue to post prohibited materials.
2011-267 of March 14, 2011 revised the mechanism provided by the Law on Trust in the Electronic Economy of June 21, 2004, and obligated Internet service providers to block access to sites containing child pornography. At the same time, the police monitor compliance with this mechanism, including by introducing into the so-called. "black list" of Internet sites that continue to post prohibited materials.
In turn, Internet providers are required not to block access to such sites, but also to filter the addresses from which such materials are received. However, the question of the effectiveness of this mechanism has been criticized, since, despite the fact that access to sites from the "black list" is indeed successfully blocked, however, the content itself is not eliminated.
Thus, serious measures are being taken at the legislative level in France to punish those guilty of child pornography quite harshly. The police and gendarmerie, however, continue to express some concerns about the existing legal delays and the reduction in the severity of punishments for crimes of cyber pornography involving children, due to the nature of "virtual" crime. In addition, some criticism from human rights activists is caused by the question of the legality of closing the blocking of some Internet resources, tightening pressure on the sphere, which may lead to infringement of the right to freedom of speech.
In addition, some criticism from human rights activists is caused by the question of the legality of closing the blocking of some Internet resources, tightening pressure on the sphere, which may lead to infringement of the right to freedom of speech.
As a police unit in France, the Central Office for the Fight against Violence operates, 90% of whose activities are focused on combating child pornography and 10% against the trafficking and involvement in prostitution of children. According to the Office, crimes related to pornography are more often committed by individuals, to a lesser extent by collusive groups.
The Directorate consists of highly qualified specialists who interact with the territorial police and gendarmerie services. The Office also performs the tasks of Interpol's central office in France.
In turn, the Central Office for Combating Cybercrime works with information and communication technologies, forms a black list of sites intended for blocking due to child pornography materials.
In addition, in his report following his visit to France in 2011, the UN Special Rapporteur on the sale of children, child prostitution and child pornography highlighted the need for competent public authorities to engage with the private sector and develop joint initiatives to combat child pornography.
Despite the existence of legal levers to counter the spread of child pornography, experts draw attention to the need for other measures aimed at preventing the exploitation of children, such as parental control over content that falls into the field of view of their children. It is also desirable: to limit the time spent by children in front of computer screens and on the Internet directly; do not allow young children to access the Internet on their own; make sure that the same online games are appropriate for the age of the child; contact providers to block sites dangerous for children; as well as reporting such resources to special control authorities.
Keep in mind that the Internet can be not only a source of useful information, but also dangerous.